The post What is Reverse Image Search? appeared first on Thinking and Meaning.
]]>
Reverse image search is a genius way to find people and images of products that aren’t readily available unless you know where to look. Image search software takes the guesswork out of finding the person or item you’re searching for and to get legitimate information on practically anything in the marketplace. However, it’s difficult to find those things unless you know how and where to look.
Why Use an Image Search Program?
If you want to find that special dress or a specific car, the Internet is a one stop shop. Shopping websites offer more products and deals than ever before. Sadly, not all of those people and products are what they appear to be. Your dream dress turns out to be doll-sized or the man of your dreams is also the man in prison or already married to two other women. Scammers take advantage of thousands of people every year, leading them to become private investigators. As the Internet grows, people turn to truth finding apps, such as a reverse image search or free reverse phone lookup app. Reverse image search can increase your chances of success by combing the Internet for images similar to the ones in your inbox.
What Is Reverse Image Search?
Reverse image search is an online tool that uses a search engine to get information, much like a word search. However, it uses a photograph to link to similar photos online. People use it to identify celebrities, to shop and, to check out people they meet on dating websites. Users can upload a picture or enter a URL into the search engine for results.
How Does It Work?
Reverse image search software can use several different methods. Some search engines target colors and the number of pixels in a picture. Others match visible textures (e.g., a brick wall) or a particular shape in the photo. The items are often referred to as a “fingerprint.” First, pictures are converted into 2D grey graphs and then used to search for similar images. Mathematical algorithms are used to compare images uploaded by users. The downside to this process is that you may end up with a photo that contains a similar background or image but isn’t related to your target subject. For example, if you are searching for a picture of a speedboat on the water, you may get a “similar” picture showing a gaggle of geese on a lake.
Online Dating
One of the most common uses of reverse image search is to identify a person. The person could be celebrity whose name you’ve forgotten or, more likely, the identity of a person you met on an online dating site. Scammers use photos of models or celebrities to trick lonely hearts out of money or personal information. Searching for those images can help to provide information on the image if the picture can be found. Therefore, image search engines can help to protect your safety.
Using Reverse Image Search
Using the search engines is easy. There are a large number of apps on the market and the list keeps growing. Following are some examples for your computer, Android, and iPhone.
PC/Mac
Google offers the most popular image search program for PC/Mac. The user can go to images.google.com to begin. Click on the small camera icon. You then have a choice to paste in a URL of the image or upload a picture from your computer. For dating sites, the best method is to save the image to your computer and then upload it into the search program. Click on the submit button to search for like images. The results will appear below the search bar.
Android
The Google platform will also work on an Android. However, users find it easier to download the Search by Image app as it is a streamlined version. The search engine works the same way, allowing you to paste in a URL or upload an image downloaded from the Internet or your camera. If you are uploading from your phone, simply choose “gallery” when it asks for the photo’s location. The rest of the process is the same as on a computer.
iPhone
iPhone uses Safari, so image searches must be done another way. The two simplest methods are to use a desktop version of the Google search engine or download a third party app that offers the same features.
Veracity and Reversee are free third party apps that allow you to search images. The apps use the same technology as Google and other popular sites but don’t require you to jump through hoops to use the Android versions.
Popular Search Engines
There are many search reverse image engines on the market, including apps. Here are the most popular:
Bing
Bing rivals Google as one of the top search engines online. Its database is one of the largest on the planet and typically offers good results.
Google Goggles
Google Goggles is an app created for Android. The app searches images and also has the ability to scan QR codes and translate text.
Google Search by Image
Google Search by Image is the most popular image search engine. Users can upload a photo or enter the image’s URL. Google offers add-ons to popular browsers like Firefox and Chrome.
Reverse Image Search
Users like Reverse Image Search for its accuracy and reliability. The app uses Bing, Yandex, TinEye, and Google to search billions of images.
TinEye
TinEye is known for its useful search results. The site uses an index of over than 12 billion images. Secondly, developers created TinEye to search images which makes it effective.
Yandex
Yandex is a search engine based in Eastern Europe and Russia. It often finds images that other sites do not.
Conclusion
If you are researching a person or item, doing extra research can pay off. Try several different apps to guarantee the best results and get the most current information.
The post What is Reverse Image Search? appeared first on Thinking and Meaning.
]]>The post Dangers of Teen Sexting appeared first on Thinking and Meaning.
]]>
Teens love their cell phones so much that they are rarely without them. They connect with people all around the world, sharing personal insights, information, photos, and more. Caught up in the moment, they often make choices that aren’t smart and can have long lasting consequences. Teen sexting is one way in which an impulsive decision can changes their lives today and for years to come.
“Everyone sends sext messages.” Teens tell each other that it’s not a big deal but they’re wrong. Kids give in to peer pressure or participate because they think it’s funny. What they don’t see is that sexting can carry serious consequences.
What is Sexting?
Sexting is sending or receiving nude pictures or sexually explicit messages through a cell phone. Teenagers engage in sexting to prove an attraction or to prevent a breakup with their mate. Statistics show that 1 in 7 teens sends sext messages; 1 in 4 receives messages. It’s common for a person to receive a message containing a nude photo or sexual suggestion. If that happens, the child should report it to a parent immediately. The parent can do a reverse lookup on the phone number to report it to authorities.
Is it Worth it?
If we have learned anything about sexting, we know it’s fun but foolish and potentially dangerous. Politicians and celebrities are often in the news because of sexting. Some have experienced ruined careers and/or ruined relationships. They tell the media they were caught up in the moment or meant no harm. In the end, the fun was not worth the consequence.
The act is particularly dangerous for young people. Kids are often drawn into sexting with strangers; people who aren’t who they claim to be. The result may be dangerous or even fatal. Even the most diligent parents can’t be on alert 24/7. Educating children is vital to their safety. Parents should talk to their children about smartphone safety, the existence of sex offenders, and sending selfies to strangers.
Sexting Statistics
Teens and politicians aren’t the only ones sending the messages:
- 12% to 16% of tweens and teens ages 10 to 19 have sent nude or semi-nude images via text message.
- 15% of teens have received a sexually explicit image through social media or text messages.
- 40% Adults 18 to 34 years old admit to sexting
- 10% of senior citizens (55 years old and older) admit to sending sexts.
- Sext messages are sent almost equally between male and females.
Legal Consequences
Drexel University published a report stating as many as 50 percent of all teens engage in sexting before age 18. The study also shows that most teens are unaware of the legal consequences of sexting. Parents must educate their kids on the risks and the following consequences:
Sexts are Forever
Teens love Snapchat. They post pictures and know that they will be gone in a matter of seconds, so what’s the harm? Teens operate social media channels better than the tech savvy experts that created them. They have learned to save and store images, regardless of where they are posted. Servers store everything that is posted on the Internet. The images can come back to haunt your teen, preventing them from getting into a good school, landing a good job, or running for office. Messages sent via text can also be retrieved, even if the number is blocked on your iPhone.
Sexting is Child Pornography
People posting nude or compromising pictures that involve a minor are guilty of child pornography in many parts of the country. Sharing the pics also known as distribution of child pornography, is considered a felony, even if the minor has agreed. People receiving the photo can also be charged. Any of the people involved, even those underage, may also be considered to be a sex offender and would have to register with the sex offenders’ registry. A recent study showed that 61 percent of teens said if they had known the facts, they probably wouldn’t have sent the photos. As with the pictures and messages, criminal charges are forever.
Sextortion
Sextortion is a form of extortion or blackmail from someone using sexually related messages or photos against the sender. It can also be an attack against the person in the photo, even if it didn’t come from their smartphone or social media account. It’s most common among teens or couples that have recently ended a relationship, although there is a rise in incidents with tweens. It happens between friends who are fighting. Also referred to as “revenge porn,” sextortion can easily embarrass the persons joining in the conversation. It may cause animosity, embarrassment, or worse. Teens can be outcast, expelled or denied access into college. People put themselves at risk, including their future careers and relationships. People need to remember that once a photo or message is on the Internet, it is there forever. You can’t get it back.
Additionally, sexting carries legal issues. The person taking or sending the picture can face fines or even jail for distributing pornography, even if that person is a minor.
Ruining a Reputation
People use photographs in many ways. The teen loses control over the image once it is sent. The photo can be used to embarrass the teen, suggesting that he or she is an easy mark for sexual conquests, i.e. “slut shaming.” Teens manipulate photos to create memes, write mean comments, and more. “Frenemies” may blackmail the teen in the photo and, too embarrassed to tell, the teen will give into demands to retain privacy.
Invitation to Sexual Predators
Sext messages are usually sent to one person, with the hope that the photo will remain private. There are no guarantees that will be the case. The recipient can show the photo to friends or post it online. Photos posted online are public domain and no one can control who will see them. A sexual predator can find the photo and, using public information, find the person in the photo.
Protect Yourself
First, you need to educate yourself about sexting, including the dangers and consequences.
To avoid the embarrassment and possible legal consequences from sexting, simply refuse. Do not take nude or compromising pictures. Do not engage in sexual conversations.
Lastly, avoid keeping inappropriate photos and videos on your computer. At the least, computers can be hacked, and private photos can be leaked to social media sites.
Conclusion
Parents must teach teens about responsible texting the social media use to protect them from the risks involved today and down the road.
The post Dangers of Teen Sexting appeared first on Thinking and Meaning.
]]>The post Should I Keep My Landline? appeared first on Thinking and Meaning.
]]>Making a Connection
Businesses need a stable source to connect with clients and vendors. They install or keep their landlines to have a link to the outside world. Landlines also support multiple handsets and phone lines.
Accessibility
Cell phone users may have trouble in rural areas. Cell phone towers don’t exist in some areas due to geography. Radio wave interference drops phone calls. Landlines can be used wherever there is a telephone pole. Landlines also offer accessibility features such as oversized keys, the ability to attach touch screens, extra loud ringer settings, voice activation for the vision impaired, flashing lights for the hearing impaired, transcription units, Braille-based devices, improved clarity, etc.
Comfort
Many people, especially seniors, say that their old fashioned phones are more comfortable than the much smaller cell phones. The handsets are much larger, which makes it easier to use while taking notes, such as typing, cooking or washing the dishes.
Cost
Landlines are cheap. You can buy a phone at a yard sale or thrift store and it will work. The cost of local service is about $30.
Security
Many homes keep landlines for security. Older people may have had their landlines for many years and the thought of changing phone numbers means notifying a lifetime’s worth of friends, family, and businesses.
Everyone worries about security. In the age of hackers, using a landline is a lot safer than using a cell phone. Landlines send data through a fixed system, where cell phone data is sent through radio waves. Hackers can get data from cell phones. In order to tap into a landline, a device must be attached to the phone and/or the line.
Cell phones introduced an important security feature with the ability to trace a phone number. Landlines now offer the same feature.
Emergency Services
Landlines make a secure, traceable connection to emergency services that cell phones and VoIP phones don’t, depending on the service and location. Callers using 911 connect to the dispatcher. The dispatcher has immediate access to your location, even if you get cut off. Cell phone users must give their location and phone number before reporting the emergency. Poor call quality can cause important information to get lost, wasting precious time in an emergency situation.
The post Should I Keep My Landline? appeared first on Thinking and Meaning.
]]>The post How Spammers Make Money appeared first on Thinking and Meaning.
]]>
People who send spam emails and text messages are in it for more than simply irritating the average person. They make money by sending fake messages or ones that encourage you to buy products – legitimate or otherwise. By law, spammers must honor all “unsubscribe” requests, but many do not. If you receive the requests on your phone, you can block the phone number, but even that may not stop the messages. You can report the activity to the appropriate authorities but it may not help much.
Creating the Bankroll
Spammers make money in several ways. The spammer collects a large number of emails to use as targets. Some send out a million or more messages per day, through email or text message. Spam artists that make the most money are often creators of scams, getting people to buy products that will never arrive. Many people will simply forget about small purchases, so the thief keeps the money. The money adds up fast. The most notorious spammers have made millions of dollars before being caught and fined or jailed.
If you think spammers are making small paychecks, consider this: Current reports show that spammers and other internet con artists make more money than drug dealers. The crooks have less chance of getting caught, especially if they use email services like Gmail or fake Internet phone numbers.
Spammers who use bot-nets or hacker-controlled systems, charge $300-$700 or more per hour.
Selling Information
Spammers also make money by stealing and selling personal information. Some spammers can get people to give out credit card numbers and social security numbers by phishing. They might pretend to be someone who works for a real company like Amazon or a government agency like the Social Security Administration. The email contains links and asks for information such as your username, addresses, password or credit card information. The spammer may use the information in order to sell it to third parties.
Spammers use a common trick to get people to enter their information. You will receive a link to a site that appears to be a legitimate site. Once you click on the link, your computer is infected with spyware, malware, or viruses. It’s an easy mistake to make because the fake site looks like the real site, except that the name is misspelled. For example, you think you’ve clicked on a link for www.amazon.com, but the fake address is www.anazon.com. Your account gets charged for any purchases you make. Unless your bank or credit card has anti-fraud protection, you may not get your money back. The spammers are smart and are usually untraceable.
Protecting Yourself
You should act as if every text message or email you get could be from a scammer or spammer. Type information into your browser instead of clicking on the links sent to you. If you receive any suspicious messages, delete them completely from your phone or computer. You should update your anti-virus, spyware and malware programs on a regular basis.
The post How Spammers Make Money appeared first on Thinking and Meaning.
]]>The post How to Recognize a Romance Scam appeared first on Thinking and Meaning.
]]>
Online dating is the number one way in which people enter into romantic relationships. Countless dating sites are devoted to people seeking love. People using the sites to find romance claim it’s a convenient way to meet someone, particularly if you live in a rural area. However, it can also mean making yourself a target for scammers. The act of posting a fake dating profile is known as “catfishing.” The reports of catfishing on dating websites has increased tenfold in recent years. Romance scam artists use dating sites and popular apps such as Plenty of Fish, Tinder, Match.com, OK Cupid, and more. “Sugardaddies” or “sugarbabies” perpetuate scams even more blatantly than on regular dating sites. More recently, scammers have been using more traditional social media sites to scam people. Examples include Facebook, Snapchat, and Instagram.
The Targets
Romance scammers are savvy when it comes to tricking their targets into sending money to line their pockets. Some ask for money right away while others work up to it, starting with iTunes or gift cards, eventually asking for credit card or bank account information. Scam artists try almost anything to get personal information or financial information. They take money from people or commit identity theft. Regardless of the method, it always comes down to money.
Victims of online dating scams suffer embarrassment when they’re duped, but it doesn’t mean they’re foolish or stupid. Scammers know what to say and when to say it to pull on a person’s heartstrings. Many will talk on the phone or text to develop an online relationship with a promise for a future together. Some promise to “meet” on Skype or FaceTime. Others make wedding plans with the scam victim. Romance scams always end the same way – the scammer takes the money and runs. The thief leaves the scam victim poorer and often heartbroken.
Primary Victims
People often think that victims of romance scams are desperate lonely hearts. The truth is that targets come from all walks of life. Reports show that millennials, seniors, professionals and celebrities fall victim to scams. Primary targets for romance scams include:
Women. Women fall victim to romance scams more often than men. Scammers target divorcees and widows most often. Con artists play upon the woman’s feelings of loneliness.
Abuse Victims. Abuse victims experience poor treatment they think of as normal. Living in denial, often for years, allows them to ignore red flags from scammers. Victims believe the romance could be real and go along instead of questioning strange behavior.
Professionals. Successful professionals portray intelligence, savvy, and worldliness. They make smart decisions to get ahead in the business world. However, they fail to make the same wise decisions in personal relationships.
Crisis Survivors. Survivors of tragic experiences look for comfort and security. Crises include losing a job, divorce, death of a loved one, medical troubles, etc. Scams target people who aren’t thinking clearly or those who have mental instability due to trauma.
Victims of Previous Scams. Romance scammers also like to prey on people who have been victimized before. You might think that being scammed once would make people more cautious in the future, but often, their response is just the opposite. The University of Exeter study found that people who have fallen for one scam are consistently more likely to show interest in another. It concluded that up to 20% of the U.K. population is naturally vulnerable to scams.
Residents of Developed Countries. Scammers prey on people around the world. They believe that residents of developed countries have more money than those in less developed regions. Romance scammers target areas like the U.S., Britain, China, Brazil, Canada, Australia, and New Zealand.
Other Victims
Secondary victims include people who are completely unaware a scam has taken place. Scammers steal names, faces, and identities of people to scam others. Dr. S. from Charlotte, NC began to receive strange phone calls and texts from women on dating sites. Dr. S. was a happily married man with a thriving medical practice. A woman reached out to him, telling him that she had seen his photo and name on several dating sites. She knew it was a scam and wanted to warn him. Dr. S. was stunned and immediately investigated. The scammer had published his full name, phone number, location, and profession. Dr. S. was able to get the information removed from the sites immediately. He was one of the lucky ones.
Potential Dangers
The FBI reports that Americans claimed losses of more than $230 million in 2016. Totals do not reflect scams that went unreported. Victims suffer from shame, embarrassment, and the fear that others will discover the story. Scammers cause additional problems for victims above and beyond financial distress. Look out for the following schemes:
Facilitating Crimes. Scammers convince victims to help them commit other crimes, with or without foreknowledge. Crimes include laundering money, receiving stolen goods, and transporting drugs.
Mental Health Problems. Romance scams cause mental problems in many victims. Victims develop severe depression, anxiety and similar mental health disorders after being scammed. Some claim that being robbed of a love relationship is worse than any financial loss. Lack of understanding and support from family and friends only worsened the condition. Others refuse to believe the relationship was a scam and continue to believe the scammer. HuffPost reports that many scam victims attempt or commit suicide.
Blackmail. Con artists resort to blackmail if victims won’t play the game. They use compromising photos and videos to threaten the target. Some scammers threaten to call the person’s boss or post sensitive information online. Victims shouldn’t expect scammers to keep their word even if they do comply.
Physical Danger. A target travels overseas to meet a soulmate. Once the victim arrives s/he is stranded in a foreign country with the potential to be kidnapped or murdered.
Ongoing Target. Victims suffer when they succumb to romance scams. Scammers use the victim’s information to create another scam or sell the information to other con artists or black market groups. Surprisingly, the victim is likely to fall for another scam, romance or otherwise, more than once.
Spotting an Online Romance Scam
Scammers give telltale signs that they are not legit. Some fake profiles are obvious, while others are cleverer in giving out as little information as possible. Red flags include:
- He insists that you leave the site and talk in person, text or email. Once you leave the site, his dating profile changes or disappears.
- The scammer rarely uses the target’s name. Instead, he uses terms of endearment like “honey,” “sweetie,” or “baby.” A common opening to a scam email to a woman is “Hello pretty.”
- The scammer has a hard time keeping personal details straight. It is common for a con artist to forget where he lives, i.e., the site says San Francisco but he says Miami. In some cases, the scammer forgets his own name or profession.
- Written messages use poor English with misspelled words and strange language, e.g., “I will love meeting you and having our life as one.”
- Messaging or texting in the middle of the night.
- The fraudster sends pictures that are taken in a professional setting or look familiar.
- The thief tells a sob story about the death of a family member. Loved one or some other tragedy. Children suffer from tragedy and need a co-parent or guardian.
- Other warning signs include claiming love at first sight.
- The scammer says that while he lives in the United States, he is working in a foreign country. This also includes people portraying themselves as members of the military.
- There is always a crisis. He is in a car accident, there is a family medical emergency, a bank or credit card has been hacked, or his phone has been broken. The crisis always requires money to repair. Sometimes the amount is small but increases with time.
- Meetings never take place. The person promises to meet in real life but it never happens. The excuses seem legitimate in the beginning but occur with regularity. The excuses become outlandish or unbelievable.
- The fraudster’s passport is being held in a foreign country and he must pay to get it back. While there was a time the corrupt politicians were Nigerian, these scams are now worldwide.
- If the target refuses to send money, the scammer becomes persistent, desperate or threatening.
- Scammers send messages straight out of a romance novel. Sometimes they don’t relate to you or the things you’ve shared. If the message sounds as if it was written by someone else, copy and paste part of it into Google. You may find that the message is a quote or used on multiple sites. Scammers become lazy and predictable.
- The scammer claims to have a prestigious job like a doctor or lawyer. In some cases, the person can be searched online for verification. Common jobs that may not be able to be traced include civil engineer on a project overseas, military commander, bitcoin trader, import/export entrepreneur.
What to Do if You’re Suspicious
- Online daters should use a reverse image search on any photos received. Google, Tineye, and Social Catfish are some of the sites that will reveal scam artists by their photos. The reverse search will show if it’s a commonly used picture or one of a celebrity. An image search shows if the profile is being used on another social media site or other dating sites.
- Ask for identification.
- Run a reverse phone search on the scammer’s phone number. The search shows if the number is a VoIP phone number, legitimate, or registered to someone else.
- No matter how much the person begs or threatens, do not send gift cards, money in any form (e.g., Western Union, Moneygram, or wire transfer), or send/receive packages. The stories can be convincing but, in the end, the person will take the money and leave the site. If the identity is fraudulent, there is a slim chance the person will ever be identified or caught.
Fighting Back
Scammers count on victims being too embarrassed to fight back. The FBI estimates 85 percent of online dating scams go unreported because the victims are too ashamed to come forward. Sadly, scammers avoid getting caught most of the time. Con artists use technology to cover their tracks.
Victims can take steps to fight back. For example:
Call the financial institution. Scammers request untraceable funds. However, if the victim used a bank or credit card, the financial institution could stop or credit the victim for the monies lost. Fraud prevention services help people reclaim money taken from accounts. Untraceable funds include MoneyGram, gift cards, and pre-paid cards.
Report the scam to law enforcement immediately. Report scams using the United States Postal Service as mail fraud. Victims of online dating scams should also make a report to the state Attorney General as well as the Federal Trade Commission (FTC) and the FBI’s Internet Crime Complaint Center.
Seek Counseling. Experts encourage victims to seek financial and psychological counseling. Financial counselors teach people how to recover from financial loss. Psychological counseling gives victims the tools to recover from the deception and heartbreak involved in a failed romance. Additionally, counselors listen without judgment and the repercussions that victims experience from family and friends.
Fight Back. New websites advocating for romance victims appear almost daily on the internet. Sites like Romancescam.com and Romancescams.org help victims fight back with support groups, information, alerts, and tools to research potential scammers.
Conclusion
Romance scams occur every day all around the world. A person seeking a relationship online must take precautions and move forward with extreme care to prevent becoming a victim.
The post How to Recognize a Romance Scam appeared first on Thinking and Meaning.
]]>The post Computer Tech Support Scams appeared first on Thinking and Meaning.
]]>
Computer tech support scams are on the rise. The scammers use the consumers’ fear by alerting them to security breaches, viruses, or ineffective software programs for malware and spyware. The target buys into the scam, worried that his identity will be stolen or worse. Scammers contact targets through phone calls, text messages, email, and pop up ads. Savvy consumers can spot the scam with the following information:
The Lead
Tech support scammers notify targets that there is a problem with their computer, such as a virus or damaged hard drive. They tell you that they can fix the problem for a fee and ask you to wire money, buy a gift card or prepaid card. They choose those methods of payment because they are difficult, if not impossible, to get back or trace.
Spotting the Scam
Con artists have different ways to trick people into believing their stories. Here are the most common ways they fool consumers.
Phone Calls
Tech support scammers make random phone calls and claim to work for a well-known company like Microsoft or Apple. They say that your computer has informed them of a serious problem and offer to run a diagnostic scan if you give them remote access. If you agree, the scammer pretends to run a scan on your computer and then tells you about a problem that isn’t real. The Federal Trade Commission has recorded one of the calls made by a computer tech support fraudster. You can listen here.
Legitimate companies will not call you to discuss an alert or ask for payment for tech support. Most companies use online support systems. If the problem cannot be solved, you can call tech support directly. If you do receive a call, use a reverse phone search on the number that called you. Write it down so you can report it to the authorities.
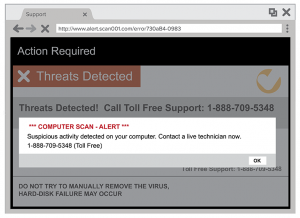
Pop-up Ads
Pop-up ads are a nuisance and can often be avoided by using a pop-up blocker. However, scammers are smart and can sometimes work around the block. The ad will pop up on your screen, alerting you to a problem on your computer, due to a failing operating system or virus. The ad might show a logo from a well-known company. It lists a phone number for you to call to get help.
Online ads for tech support are always suspect. If you haven’t had any problems with your computer then ignore the ad. If you think that your software might be outdated, run an update on your system and then perform a scan.
Improve Security
Scammers love weak passwords. Change your password on a regular basis. You can create a complicated password or use a password generator to improve your computer’s security.
Reporting a Scam
Consumers don’t always report scams because they are embarrassed. They may not know that they have been scammed. If you suspect you might be the target of a computer tech support or other scam, report it to the Federal Trade Commission’s Complaint Assistant.
The post Computer Tech Support Scams appeared first on Thinking and Meaning.
]]>The post Tips for Avoiding Business Scams appeared first on Thinking and Meaning.
]]>
Scammers target businesses as much, if not more, than individuals. One of the biggest scams is charging businesses for items they did not order, or unordered sending items along with an invoice. The scammers count on the fact that in some businesses, the person ordering the items isn’t always the person handling the invoices. The scam goes unnoticed and the scammer receives a fat check. If the order is not refused or returned, the scammer will go in for the kill with a bigger order and matching invoice. People operating small businesses have the advantage since they usually know what was ordered as well as which invoices are legitimate. A one man show may use his personal cell phone to conduct business which allows him to use an app for unknown number look ups and to reverse search calls from suspicious vendors.
The scams target many different types of business and non-profits, including mom and pop businesses to churches to corporations. The Federal Trade Commission has reports on various types of scams, how to avoid them or report the persons responsible for the scam. Their website reports one company that had paid out over $20,000 for supplies they never ordered – light bulbs, cleaners, hand sanitizers, etc. Some companies refuse to pay for unordered products, which is legal; otherwise they would have to pay to return them to the sender. If your business receives products or merchandise that no one ordered, the law says the vendor cannot charge or legally collect on it. You don’t have to pay for it or return it, even if the products were used.
Protecting Your Business
Business owners can protect themselves from merchandise scams by doing the following:
Train Employees
Scammers may target more than one employee in a business. Train employees to direct calls to a purchasing agent or manager.
Checks and Balances
All purchases and invoices should be checked upon arrival. If an item arrives that was not purchased, it should be investigated.
Verify Invoices
Business owners should always verify invoices and requests for payment. Any unknown person that offers to pay by personal check could be suspect. If someone requests payment via wire transfer, gift card or reloadable gift card, it’s almost certain to be a scam.
Be Tech-Savvy
Scammers are clever. Don’t trust your Caller ID. Thieves can obtain fake phone numbers and emails that are usually untraceable. They may send messages that appear to be from clients or colleagues, so you should always verify. Keep your organization’s financial information, passwords and files in a secure location. Avoid opening emails with attachments as they may contain viruses or spyware. The FTC has more tips on keeping your business safe at Small Business Computer Security Basics.
Beware of “Consultants”
Before hiring a business consultant, research the company. It is a trend for fake consultants to demand upfront payment and then not show up or offer advice you could have had for free.
While it may seem impossible to stay 100% safe, being vigilant can certainly help to protect your business.
The post Tips for Avoiding Business Scams appeared first on Thinking and Meaning.
]]>The post Why Are the Police Calling Me? appeared first on Thinking and Meaning.
]]>
When you receive a call from the police, the first instinct is that something is wrong. You’ve done something wrong, someone needs bail money, or there has been an accident. Secondly, there may be a solicitation from a police charity such as a fundraiser. Someone may request support for the local Sheriff’s department or Fraternal Order of Police (FOP). While all those things are legitimate, some are not typical. For example, if you have broken the law, the police are not going to call you. They will come to your house and arrest you. If bail money is needed, the person needing the money would call, not the police. Fundraising efforts do take place, but you should insist on supporting local organizations only, ones that can be verified.
Here are some common scams related to law enforcement:
Arrest Warrants
Police issue arrest warrants if someone has broken the law. Law enforcement refers to is as a “bench warrant.” It is a document stating that you must go to jail immediately. Police never call criminals to let them know they will be arrested. Victims of arrest warrant scams are told that they must pay a certain dollar amount or be sent to jail. The scammer requires you to send money via Western Union or another wire service. Don’t do it! Call your local police station immediately.
Jailbird Relative
Seniors are common targets of this scam, often referred to as the Grandparent Scam. The caller contacts a senior to say that a relative is in jail, usually in a foreign country. They require the victim to pay a large sum immediately or the relative will be held without bail. The caller never offers proof of the arrest. They may say that a bondsman will call shortly to arrange for the bail to be paid. If the caller presents himself as an officer, ask for his name, rank and badge number. Call the local authorities immediately if you receive this type of call.
Police Charity
Police and fire departments are sometimes underfunded. As a result, they will solicit funds from the public. Citizens may receive a call asking for donations for a specific event or to support the Fraternal Order of Police. Police will never ask for credit card information over the phone. If you are suspicious of the request, contact the organization directly.
Detecting a Phone Scam
It may be difficult to identify a phone scam but it’s not impossible. Scammers use fake names and a spoofed caller ID to hide their real phone numbers. Also, scammers can tap into phone numbers used by police so that they appear legitimate.
Ask for Information
If a police representative asks for money, ask questions. Callers should give you their full names and the organization’s address. If the caller says they are collecting for a specific chapter or precinct, call to verify before opening your wallet. Scammers usually can’t answer any questions, get defensive and/or hang up.
The post Why Are the Police Calling Me? appeared first on Thinking and Meaning.
]]>The post Who is Texting Me? appeared first on Thinking and Meaning.
]]>
We live in a society of convenience – convenience stores, online shopping, and sending text messages. Scammers use conveniences to find and trap new victims. Thieves steal information from people through a technique known as “smishing.” Smishing is a scam like email “phishing” scams – receiving fake emails from your bank, phone carrier or other companies. Smishing is sending the same type of message – one that you are likely to answer – via text message. If the person receiving the text answers, it is easy for scammers to steal identity or other information. They can plant viruses or worse from that one simple reply.
The Federal Trade Commission (FTC) reports that identity theft scams are on the rise. Their advice to consumers is to ignore and delete the messages without a reply. If you receive a text that seems suspicious, it is also wise to block texts on your iPhone from that number.
Scare Tactics
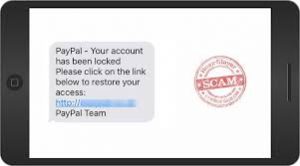
Scammers use fear and intimidation to lure their victims. The text messages could revolve around anything from unauthorized use of a bank account to account activation. Other tactics include contests, prizes, or fake job offers. A scam message may look like:
A transaction has been processed on your Bank of America account. If you did not make this transaction, reply “unauthorized” to this message.
Or
New jobs at Amazon.com located in your area! Reply “interested” to receive more information.
The scammer relies on the reply to be able to get your information.
What Can They Do?
Hackers are dangerous. They can access your personal information including bank account and credit card numbers. They can also install viruses, or worse, keylogging software. Keylogging software is a type of malware (virus) that can be installed on a phone or computer. It keeps track of every keystroke or entry made into the device. It can track every message sent, every password, and all account information. The software is installed in the system and can be extremely difficult to remove.
Unsolicited Text Messages Aren’t Always Illegal
It is illegal to send unsolicited text messages, unless the texting party has a relationship with the recipient. Companies such as your bank, phone service provider and other businesses you use can send messages unless you opt out of the service. Political campaigns and charities soliciting funds are exempt from the rule.
Federal law states that “robocalls,” services using computers to call random numbers or mass auto-dialers are illegal.
Text Safety Tips
Text safety tips include:
- Users should not reply to the text – even if it gives you an option to be removed from the list.
- If you feel the text is legitimate, check it out before responding. Call your bank or other company directly. Scammers require an immediate response.
- Never click on links or phone numbers.
- Delete the message immediately.
- Report the message to your phone service carrier.
The post Who is Texting Me? appeared first on Thinking and Meaning.
]]>The post Medicare Phone Scams appeared first on Thinking and Meaning.
]]> T
T
Medicare, like most health insurance plans, has an annual enrollment. It takes place from October 15 to December 7 each year. When the time draws near to that date, members get phone calls from people who say they work for Medicare. The calls regard upgrading or buying insurance. The bad thing is that insurance can be confusing to the insured. Scammers like to target the elderly who may not understand their benefits.
New Medicare Cards
Medicare used Social Security numbers (SSN) to identify beneficiaries and health insurance claims. In April 2018, CMS began distributing new cards without SSNs. Instead, the new Medicare cards use a unique number which should be protected. Members give the number to medical providers, insurers acting on the member’s behalf, and trusted people in the community, such as State Health Insurance Assistance Program (SHIP) counselors.
It is important to note that members do NOT need to update information, pay a fee, or “activate” their new cards. The agency mailed cards automatically.
Four Parts of Medicare
Members can avoid fraud by understanding Medicare. Understanding the four parts of Medicare is simple unless someone is trying to confuse you. Before talking to anyone about your plan(s), be sure to know what parts you have. Educating yourself in that way will make spotting a scam much easier.
Part A
Part A, coupled with Part B, this is often referred to as “the original Medicare.”
- Inpatient care in a hospital
- Inpatient care in a skilled nursing facility (not custodial or long-term care)
- Hospice care
- Home health care
- Care in a religious non-medical healthcare institution
Note: Part A does not offer full health care coverage.
Part B
Part B is considered a necessary partner to Part A.
- Includes regular doctor visits
- Covers medically necessary services (e.g., wheelchairs or surgeries)
- Preventive health care services, like lab tests and screenings
Part C
Medicare Part C, aka “Medicare Advantage” combines Medicare Part A and Part B. Plans commonly offered:
- Health Maintenance Organizations (HMO plans)
- Preferred Provider Organizations (PPO plans)
- Private Fee-for-Service (PFFS plans)
- Special Needs Plans (SNP plans)
Part D
Part D is Medicare’s Prescription Drug Plan (PDP):
- Helps to cover the cost of prescription drugs
- May help lower prescription drug costs and protect against higher costs in the future
Common Medicare Scams
Most of these scams take place over the telephone, but some do happen through email, U.S. mail and door-to-door visits. Callers steal a person’s identity by making up stories to try to get their name, Social Security number (SSN) or financial information.
Scammers are ruthless. They will say anything to get your information, including your bank account or social security numbers. Many scammers pick seniors who need Medicare to live. Some common scare tactics:
- Caller states that you will lose your coverage unless you join a specific plan.
- Attempts to get you to say “yes” to something.
- You must pay to get a new Medicare card. This isn’t true. Medicare cards, even temporary ones, are free and are sent automatically.
- Attempts to “verify your identity.”
- Someone says you that you must give updated personal information to get a new or updated Medicare card. .
- Fake offers for “free medical supplies.”
- A caller will offer medical equipment and says that “Medicare will cover it.” They ask for your SSN or Medicare Number and/or payment to cover shipping and handling costs for the “free” supplies.
- False claims that you’re eligible for a “refund” or “rebate.”
- Claims you must share information or have your benefits canceled.
- Attempts to get you to enter sensitive data through a fake website link.
- Scammers may send “phishing” emails to get your information
Sensitive Information
Scammers need certain information to steal your identity or to fill out forms on your behalf. They will try to get the following information from you:
- Date of birth.
- Birthplace.
- Mother’s maiden name.
- Social Security number.
- Medicare number
- All or part of your credit card number, including expiration date and security code.
- Your bank account number(s).
Identifying Fake Calls
Scammers aren’t always easy to identify. They get information about the people they call before any a call is made. They may have your full name, mailing address, birthdate, and phone number. The caller may sound professional, sympathetic, and knowledgeable. Others may speak in a foreign or broken accent, which makes them easier to spot. No matter what a person says, never give out personal information. Medicare rarely calls and will never ask for financial information. If you must be contacted, they will send a letter to make an appointment.
If you ever doubt the validity of a phone call, say you’d like to call the person back and ask for their direct number. A real person will respect your desire for privacy and security.
Medicare and the SSA
The elderly is most often targeted by scammers claiming to be from Medicare or the Social Security Administration (SSA). Here are some important things to know about how those agencies work:
Medicare won’t call you, except in limited circumstances. Someone will call if you have called 1-800-MEDICARE and requested a return call. However, if you have called to join a Medicare Advantage Plan (Part C) or Prescription Drug Plan (Part D), you may be asked to give information over the phone. No one should ask for financial information.
- Representatives will never call or come to your home to sell products or services.
- SSA representatives may call Medicare beneficiaries if they need more information to process applications for Social Security benefits or enrollment in certain plans, but, again, this is rare.
- The SSA sends letters to set up a telephone interview.
- Medicare cards do not expire.
- Contact the SSA directly to get a replacement if your card is lost or destroyed. If you think someone else is using your Medicare card, then call Medicare
Have You Been a Target?
If you suspect a scam or receive a call by someone stating to be a representative, use an iPhone app to search by phone number. Hang up immediately if the number is blocked, restricted or unavailable. People should report fraud immediately to StopMedicareFraud.gov, or call the agency directly at 1-800-633-4227. If you have provided personal information to a scam caller or think you might be a victim of identity theft, report it to the Federal Trade Commission (FTC) at IdentityTheft.gov or by calling the ID Theft Hotline at 1-877-438-4338.
The post Medicare Phone Scams appeared first on Thinking and Meaning.
]]>The post Is Your Partner Cheating? appeared first on Thinking and Meaning.
]]>
How to Tell if Your Partner Is Cheating
There is a theory that technology has made it easier for partners to cheat. People can meet via social media, texting and dating websites, and have little chance of getting caught. That is, unless the other partner is savvy. There are dozens of ways your partner’s fidelity can be verified if you are willing to invade his or her privacy.
Caller ID
Checking the caller ID on a person’s phone is the easiest way to find out who has been calling (or is being called). If the person’s name does not appear on the screen, you can use an iPhone number tracer app to get information.
GPS Trackers
GPS trackers are an efficient way to find out where your partner is going and when. You can hide a tracker in a vehicle or you can use a phone app. The person is unaware that he is being tracked.
Spy Apps
There are dozens of spy apps on the market. The free apps make more promises than they can deliver but it depends on your needs. Several sites tout these at the top 3 spy apps for Android and iPhone:
- mSpy – offers Geo-fencing (targeted “safe zones”), keystroke logging, web and app activity, ability to block specific websites from the user’s phone.
- Highster – the most budget-friendly. Highster offers tools to monitor children and employees. It allows users to perform GPS Tracking, Call Tracking, Access Photos & Videos, View Browsing History, Social Media & App Tracking, SMS Text Messages, and Phone Camera Control.
- Flexispy – works on both iPhone and Android. Offers the most powerful features including: Track and Intercept Calls, Record Phone Calls, Ambient Listen Mode, Remote Camera Control, Spy on Text Messages, Spy on iPhones, Androids, Nokia, and Blackberrys.
Statistics About Infidelity
- 2% to 3% of all children are the result of cheating.
- 30% to 60% of all married people in the U.S. will cheat
- 33% of marriages have one or both partners having an affair.
- 35% cheat on a work trip
- 36% of men cheat with a coworker.
- 40% of online cheating turns into real life cheating.
- Cheaters are 3 times more likely to cheat again.
- Cheating usually occurs 2 years into marriage.
- Infidelity is increasing among people under 30. Many experts credit this to opportunity, being away from home and early sexual activity.
- Men are more likely to cheat, however, that is changing as women continue to become more financially independent.
- Cheating is rarely uncovered.
- Polyamory, being romantically involved with more than one person, is increasing in popularity.
- Technology increases the opportunity to meet someone else.
- People may cheat when they are bored.
- Emotional infidelity can be as damaging as physical infidelity.
Keep in mind that while these apps can give you the proof you need of infidelity, the information is not generally admissible in court.
The post Is Your Partner Cheating? appeared first on Thinking and Meaning.
]]>The post Are You Being Catfished? appeared first on Thinking and Meaning.
]]>
You’ve probably heard the term “catfish,” especially if you are on any form of social media or dating website or app. Catfishing is the act of pretending to be someone else, real or fictional, to trick an unsuspecting victim. There is more than one reason for catfishing someone online. Perhaps the other person is jealous, trying to catch a cheating partner, or doing it as a form of cyberstalking or cyberbullying. However, the one doing the catfishing is most likely trying to scam his or her victim.
How It Happens
Social media sites are rife with people on both sides of the catfishing scheme. While dating sites are most often the trolling place for scammers, other social media sites like Facebook, Snapchat, and Instagram are also possible sites for the tricksters. For argument’s sake, let’s use an example from a dating site.
Sally signs up for a dating website. She posts her picture and some information about herself. Soon, Sally starts to get messages from people interested in talking to her. At first, Sally is excited. She looks through pictures, at information and answers a few messages. Then she notices some of the people are behaving in a strange manner. Here are some of Sally’s red flags:
No profile picture.
Several of the men contacting Sally don’t have a profile picture posted. A small percentage may have a legitimate reason for not having a picture, such as a high-profile job, but more often than not, the poster may be married or not who he claims to be.
He looks like a movie star
He just might be. If a photo looks over done or professional, chances are it’s not real. Use a reverse image search in Google to uncover the user’s true identity. Some of the most popular services include Google Reverse Image Search or TinEye. Upload the person’s picture and search. Try more than one service to make sure that the picture isn’t located elsewhere on the internet. You may find it linked to other dating websites as well.
Bad English
Scammers are typically non-native English speakers. It becomes obvious quickly when chatting via message. They often use incorrect words, the wrong tense, or confuse things such as there, they’re and their. Also, non-English speakers tend to not use contractions. The lack of good grammar is a glaring sign that someone is not who he claims to be.
The Same Old Story
Scammers aren’t very creative. Sob stories generally include the person losing his entire family, being stranded overseas, or having lost his wife to cancer and left with a child to raise. If a story sounds familiar, enter some of the text into a Google search. You might be surprised at what appears on your screen. The same can be said for overly produced poetry he uses to profess his love.
From 0 to 60 in a minute
Scammers aren’t patient. They want to gain your trust and get your money as soon as possible. For that reason, they tend to go to any length to win your trust and affection. Poetry, gifts, words of affirmation and love are just some of the ways in which a scammer will try to win you over. The more you accept those gestures, the harder the scammer tries.
The Ask
Once a scammer feels he has your trust, he will ask for something. It usually starts as something small, a small token of your affection. He may even send the first gift to get the ball rolling. Perhaps it’s simply a phone call or video chat. Rest assured that it’s only the beginning of something much bigger.
Common requests:
- Airline ticket. He tells you that he is stranded overseas or wants to visit you, but is short of cash. He says he has had a medical emergency or has been robbed. You have to pay for his ticket and as soon as he arrives, he will pay you back. The problem is that once the ticket is sent, he never arrives, and the money is gone.
- Financial emergency. There has been an accident. The rent or insurance is past due. He was wrongly terminated from his job. He only needs a small loan.
- Make a trip. He can’t visit right now, but you can make a trip to see him. Risks include being stood up at the airport, stranded in a strange city or country or being accosted by a stranger. The least of it is being out the money for the airfare.
- Send money/packages. Some scammers benefit by convincing their partners to send money to a third party or forward a package. While it may seem harmless, it could land you in legal trouble.
Take Steps to Protect Yourself
Follow these steps to protect yourself as much as possible.
- Use a VoIP phone number or email set up specifically for the dating site.
- Download an iPhone app to find a name by phone number that will allow you to record, block and/or trace phone numbers.
- Never send money to a stranger.
- Insist on seeing a picture. Use an image search to verify identity.
- Approach the situation logically and discuss it with a trusted friend before making any decisions.
- Beware of sharing personal information about yourself, your job or your family.
- Always meet in a neutral, public place.
- Get to know the person in real life situations before giving your complete trust.
The post Are You Being Catfished? appeared first on Thinking and Meaning.
]]>The post Trading Cash For Love appeared first on Thinking and Meaning.
]]>
A great deal has been written about online dating scams. What it boils down to is scammers trying to trade cash for love; convincing lonely hearts that they will live happily ever after – for a price. Most schemes aren’t so blatant but as the availability of marks increases, the less time a scammer is willing to spend to get inside your wallet. There is no way to calculate how much money a short con can generate, but it must be good enough to avoid getting a real job.
The Set-up
The beginning is almost always the same. Person X receives a flirt or message from Person Y on a dating or social media site. Contact is made, and the dance ensues. Make no mistake – the scammer may be male or female. From what my male friends tell me, females are much worse and not shy about making up front demands.
Within a short period of time, you will know the scammer’s story. The one thing you can be sure of is that the story – and persona – are almost always fake. Catfishing, i.e., posing as someone else, is almost a given in these cases. Almost immediately, the scammer begins to profess admiration and love for you. The more lavish the attention, the more likely the target is to fall for the ruse, eventually opening his/her wallet, bank account or credit card. The ending is never happy.
Lonely Hearts
Most of the scammers have a sob story. My spouse died; I’m deployed overseas; I was left at the altar; and so on. They will say anything to tug at your heartstrings.
Emergency Cash
Inevitably, there will be an emergency in which the scammer needs fast cash: hospital bills, eviction, and broken-down vehicles are examples.
Travel Expenses
Some make grand promises to visit, if only they had cash for travel. A good friend works for an airline and will offer to cover the expenses. The scammer never accepts and wants to purchase her own ticket on his dime. My personal favorite is the scammer who is overseas and cannot access his bank account until he gets back to the States. It’s true that there are banks and credit cards that place travel bans on accounts but they aren’t going to leave you stranded in some third world country.
Business Deal
An offer of a business deal or employment is a savvy way to get someone to shell out cash. Pay now, play later. The scammer may offer a partnership or a scenario of building a future together.
How to Protect Yourself
The first thing I do when interacting with someone is to search online. An app for unknown number look ups, reverse image searches, and social media accounts are a good way to start. If the scammer regales you with a sob story or flowery poetry, copy part of it and Google the words. Chances are you’ll find a matching entry. In the end, there’s nothing wrong with online dating. Most of us do it. But no matter what he or she says, keep your wallet firmly closed until you’re convinced it’s the real thing.
The post Trading Cash For Love appeared first on Thinking and Meaning.
]]>The post Top 5 Packing Hacks For Your Next Trip appeared first on Thinking and Meaning.
]]>Wether you’re taking a weekend trip or heading on a 6 month journey it’s important to pack right. Nothing is worse than getting to your destination and realizing you forgot an essential.
Here are the top 5 packing hacks for your next vacation.
1. Make a list.
This one might seem obvious, but it’s important to make a list before you start packing. Not only will this allow you to plan what you’re going to wear ahead of time, but it will also prevent you from overpacking. The less you pack, the more room for souvenirs.
2. Roll, don’t fold.
Rolling your clothes when packing them will give you more room, and prevent them from getting wrinkled while in your suitcase.
3. Bring functional clothes and layer.
Choose to bring clothes that you can layer and wear in different ways. Check out this women’s shawl wrap that can be styled as a wrap, poncho, scarf, or shrug. There are also wraps that can be worn as dresses or skirts and pants that convert to shorts.
4. Wear your heaviest pieces on the plane.
No one wants to pay overweight bag fees. If you’re going somewhere cold and need boots or a heavy jacket, wear them with you on the plane. Don’t wear your lightweight sneakers and check your hiking boots.
5. Skip the personal items.
Shampoos, conditioners, lotions, and other creams and liquids will weigh down your suitcase. Instead of bringing them, buy them at your destination. You can oftentimes find these things at airport drug stores in travel sizes.
With these 5 tips you’ll be able to avoid bag fees the next time you fly and you’ll remember all the essentials.
The post Top 5 Packing Hacks For Your Next Trip appeared first on Thinking and Meaning.
]]>The post Holiday Phone Scams: What You Need to Know appeared first on Thinking and Meaning.
]]>Romance Scams
Online dating is popular during the holidays. It’s cuffing season after all! If you’re using online dating and feel like you’ve met a special someone, make sure they’re not out to scam you! Romance scammers are quick to profess their love and then they’ll claim to be in trouble.
If your new love interest won’t meet you in person, or even Skype with you, this is a red flag. Don’t trust them, and definitely don’t share your personal and financial information with them.
Utility Scams
Imagine having no heat over Christmas. For many people in the U.S. this would not only be a nightmare, but potentially very dangerous as temperatures in the northern parts of the country go well below freezing.
Scammers, knowing this, will call pretending to be from local energy companies and they will threaten to cut the power or heat if a payment isn’t received. Many victims will panic and share their credit card information without a second thought.
Charity Scams
Many people are in a giving spirit during the holidays. Scammers will call posing as charities and soliciting donations from people during the Christmas season. These charities can range from cancer foundations to children’s organizations.
Whenever you want to donate money you can check to make sure that your donations will go towards what you want it to. You can use Charity Navigator to check charities ratings and what they use their donations for.
How to Protect Yourself
The best way to protect yourself is to user an iPhone phone number tracker tool to protect yourself from receiving these unwanted calls during the holidays. This time of the year is often stressful enough, so there’s no reason to make it worse by adding the extra aggravation of these annoying calls!
The post Holiday Phone Scams: What You Need to Know appeared first on Thinking and Meaning.
]]>The post How To Protect Yourself From The IRS Phone Scam appeared first on Thinking and Meaning.
]]>What Is The IRS Phone Scam?
There are many variations of this scam, but the most common variation is as follows. You receive a call or an automated message from someone claiming to be an IRS agent. The caller or message will say that it’s very important that you contact with them immediately in order to resolve an issue with back taxes.
They will threaten you with legal problems saying that you will be brought to court, or in some cases even arrested. The scammer will demand that you pay the taxes that they claim you owe immediately.
Why Is It Successful?
It’s no secret that taxes are complicated! Scammers know this and they take advantage of it. It’s also no secret that many Americans pay their taxes late or don’t even pay them at all. This scam also frequently targets immigrants and threatens to deport them because they owe taxes.
Many people fearing deportation or legal problems will panic and pay the scammers what they are asking for without questioning the legitimacy of the caller.
To make the scam more believable scammers will often use caller ID spoofing to make it seem as if they are calling from the IRS.
How To Protect Yourself
The best way to protect yourself from the IRS phone scam is to know your rights! (And try to pay your taxes on time!) You should know the following:
- You’ll always receive a notice of owed taxes via snail mail before you ever get a phone call.
- You always have the right to dispute what you owe with the IRS.
- You’ll never have to pay owed taxes via wire transfer or pre-paid debit/gift cards. This is the most common way in which phone scammers request money be sent.
By keeping these things in mind you can protect your information and your money. If you ever have any doubts about a phone call you’ve received consult an iPhone cell phone number look up app. These useful apps will help you identify whether or not a number has been associated with a scam.
Additionally, if you ever think you might have been contacted by an IRS scammer you should contact the Treasury Inspector General for Tax Administration and report it.
The post How To Protect Yourself From The IRS Phone Scam appeared first on Thinking and Meaning.
]]>The post Why You Need to Try Online Dating and Reverse Phone Lookup Apps appeared first on Thinking and Meaning.
]]>Why Try Online Dating?
It’s possible that you’ve just gotten out of a relationship or maybe you’re shy. No matter what your situation is you can meet new people that you normally wouldn’t meet via online dating.
No matter what your interests and tastes there is probably an online dating site or app for you. What’s important though is that you remember to stay safe while meeting new people.
Ways To Stay Safe
You might have heard people say that online dating isn’t safe, but that’s not the case as long as you are smart about it. Here are the best ways to stay safe when using online dating:
- Be cautious of people who tell you that they are falling in love with you after only a short time speaking. Romance scams are very common and a tell-tale sign of a romance scammer is someone who professes their love after only a few days of knowing each other.
- Don’t share personal or financial information with someone you’ve just met. This one seems like a no brainer, but studies have shown that we are much more likely to be open online. The online disinhibition effect is a real thing!
- Only meet with someone for a date in a public area the first time you are seeing them. Doing so will allow you to see what the person is like in real life.
- Use a reverse phone lookup app or do some other form of research before meeting anyone in public.
Why You Need To User A Reverse Phone Lookup App When Dating
As mentioned above it’s important to stay safe when dating and using a white pages iPhone app to verify the identity of the person you’re meeting is the best way to do so. By using an app like this or running a quick Google search you’ll help yourself avoid catfish, romance scammers, and even violent criminals.
The post Why You Need to Try Online Dating and Reverse Phone Lookup Apps appeared first on Thinking and Meaning.
]]>The post How To Stop Telemarketers appeared first on Thinking and Meaning.
]]>How To Stop Telemarketers
Though there’s no way to stop telemarketers completely there are a few different ways that you can reduce the amount of unwanted calls you’re receiving. Follow these steps to cut down on the calls you receive:
- Make sure your phone numbers (home and mobile) are on the FTC’s Do Not Call Registry. Once you’ve added your number to the list telemarketers can’t call you legally after 31 days have passed. There are a few exceptions though, these include political, charity, debt collection, informational calls, and telephone survey calls. Unfortunately, you’ll still receive these types of calls, but unwanted sales calls are illegal.
- Stop giving your number out to retailers. Stop giving your personal phone out to retailers when they ask for it. It’s unnecessary information that is usually sold to third parties.
- Stop using your number on surveys. Similarly, we’ll often participate in survey that request a phone number. Again, these survey companies will sell information to third parties.
- Don’t post your phone number in your social media. So many people have there phone number publicly displayed on Facebook, LinkedIn, etc. Fix your privacy settings on your social media profiles so that your phone number isn’t public.
- Check what information is available on you online. It’s always smart to run a quick Google search on your phone number every now and then to see if there is any information available on it. If there is you can contact the website and request that it be removed.
Using Phone Number Tracing Apps To Stop Them
You can also use an iPhone phone number lookup to filter your calls and cut down on the amount of spam calls you receive.
The more you interact with unwanted calls, i.e. answering them, pressing buttons when they call, getting angry and yelling at them, the more they will call you. Trust us. It’s not worth your time to talk to these people.
Instead, use an app to look up phone numbers and see what other people are saying about them. Chances are that they will be calling a lot of other people and annoying them from the same number. Additionally, many of these apps have spam blocking features that will automatically block unwanted calls.
The post How To Stop Telemarketers appeared first on Thinking and Meaning.
]]>The post Top Productivity Apps appeared first on Thinking and Meaning.
]]>
Clear
That satisfying feeling of crossing out a task is now available in a simple but powerful app. Clear is a task organizer app that lets you segment your to do’s into whatever order you prefer. Work, family, personal, friends – name it. It is customizable and all you have to do is swipe right once you’re done with a task.
Google Drive
For the most obvious reasons, Google Drive is one of the best cloud storage options for your files and a great tool for collaborations as well. This app will let you finish work even without a PC!
Connect
Connect is perfect for those who regularly meet other people. All you need is the email address of a person, and the app will look for its public profile and details with photos. When the time comes that you need to reconnect with this person, you don’t have to go through tons of business cards and worry if it’s the right person or not.
CallerSmart
Who’s ever received an unwanted call from an unknown number? Everyone. Aside from these calls being annoying, it also wastes your time! Callersmart will help you block calls on your iPhone so you don’t have to worry about getting scammed or receiving pesky spam calls.
Snowball
Let me guess, you have Facebook Messenger, Skype, Whatsapp, Viber, and all the other instant messaging apps there is. The stream of notifications must be difficult to keep track of at times. Snowball curates all your messaging and emails in one inbox, makes it easier for you to read and reply. Instead of clicking on several apps, Snowball saves your time and energy because everything is in there.
Go check out these apps today!
The post Top Productivity Apps appeared first on Thinking and Meaning.
]]>The post Features Of The Best Phone Tracer App For iPhone appeared first on Thinking and Meaning.
]]>This type of app is crucial if you are a parent and you would like to monitor who’s calling your child. It also comes in handy if you receive a lot of spam calls. It will help you reduce the amount of nuisance calls you get by helping you identify which calls you should be taking and which ones you should ignore.
How The Apps Work
A good phone tracer app for iPhone should be able to identify the majority of phone numbers that you search in it. These numbers are usually going to be a mix of landline numbers and cell phone numbers. The apps will typically use feedback from their users, plus exclusive databases to identify a phone number.
The type of information that you will receive when looking up a number should include the owner’s name and a location. This might be an exact address or a location based off of the phone number’s area code and exchange. Some apps will give you information like a picture and the social profiles associated with a phone number.
How To Use The App
The app should be easy to use. There is no need to be a tech genius to use a reverse phone lookup app. When you get a call from an unknown number copy and paste it and open up the app. The app should automatically start a search on the phone number.
After the search, the app will show you if there are any free results. Most apps will let you leave your feedback on a phone number. This helps others in your community to identify and avoid unknown calls. You will find a lot of feedback on phone numbers in a good phone tracer app.
Is The App Expensive?
Most of these apps are free, but will offer in-app purchases. It’s up to you to decide whether or not you want to pay for information on a phone number.
The post Features Of The Best Phone Tracer App For iPhone appeared first on Thinking and Meaning.
]]>
